
The Firewall Chronicles
Issue #18 | Based on true defense events
A real-world cybersecurity defense story. When sophisticated attackers probe our defenses, the Guardian Posse springs into action. Every panel contains lessons learned from actual incidents - wisdom forged in digital fire.
Start ReadingThe Firewall Chronicles

Security Operations Center at 2:47 AM. Alert screens flashing red. The night shift operator spots anomalous traffic.
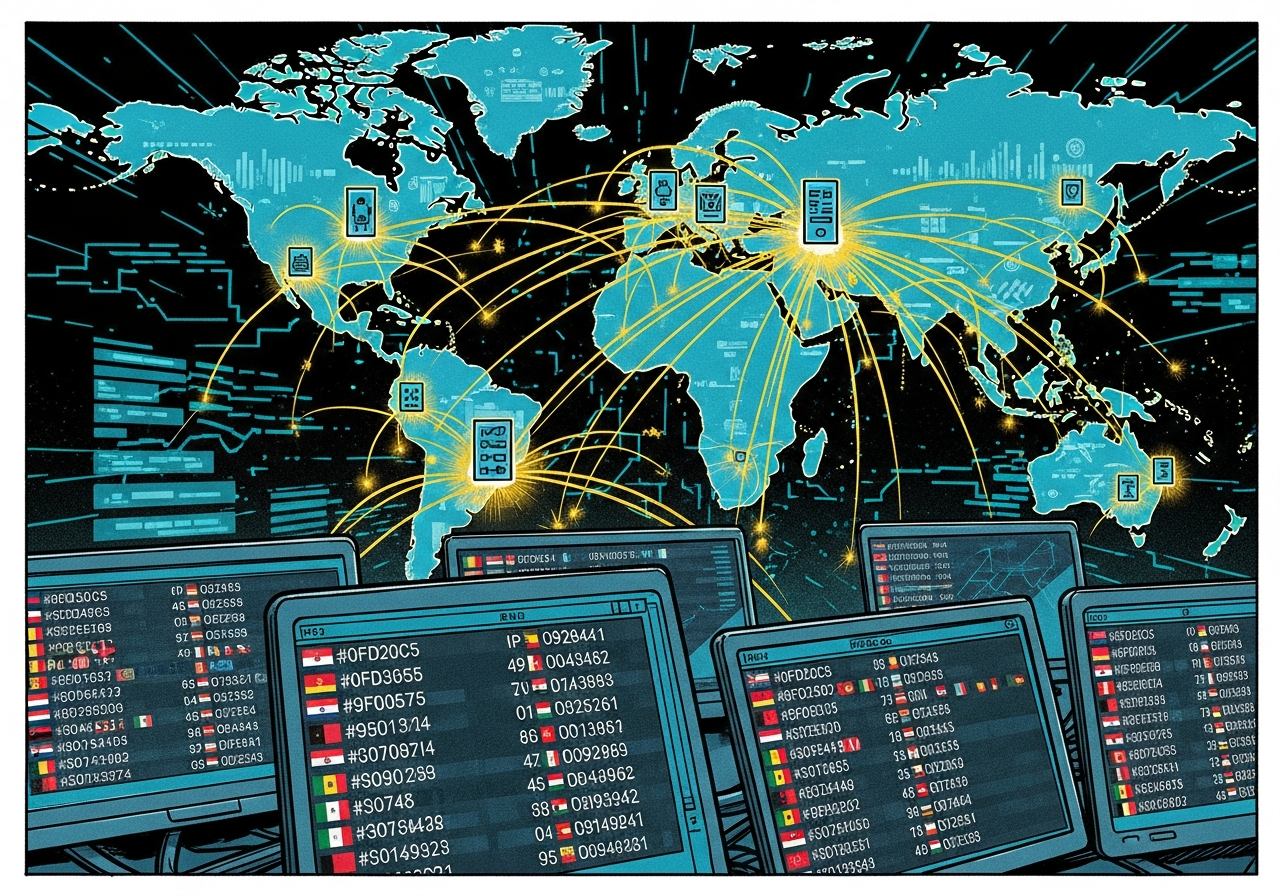
Firewall logs scrolling rapidly. IP addresses from multiple countries hitting the same endpoint.
Security Sentinel materializing from the code, shields activating.
Attackers switching tactics. Credential stuffing attempt with leaked password database.

Data Intelligence Agent analyzing login patterns, detecting impossible travel scenarios.

Multi-factor authentication prompt blocking the stolen credentials.

Attackers attempting SIM swap social engineering at telecom provider.
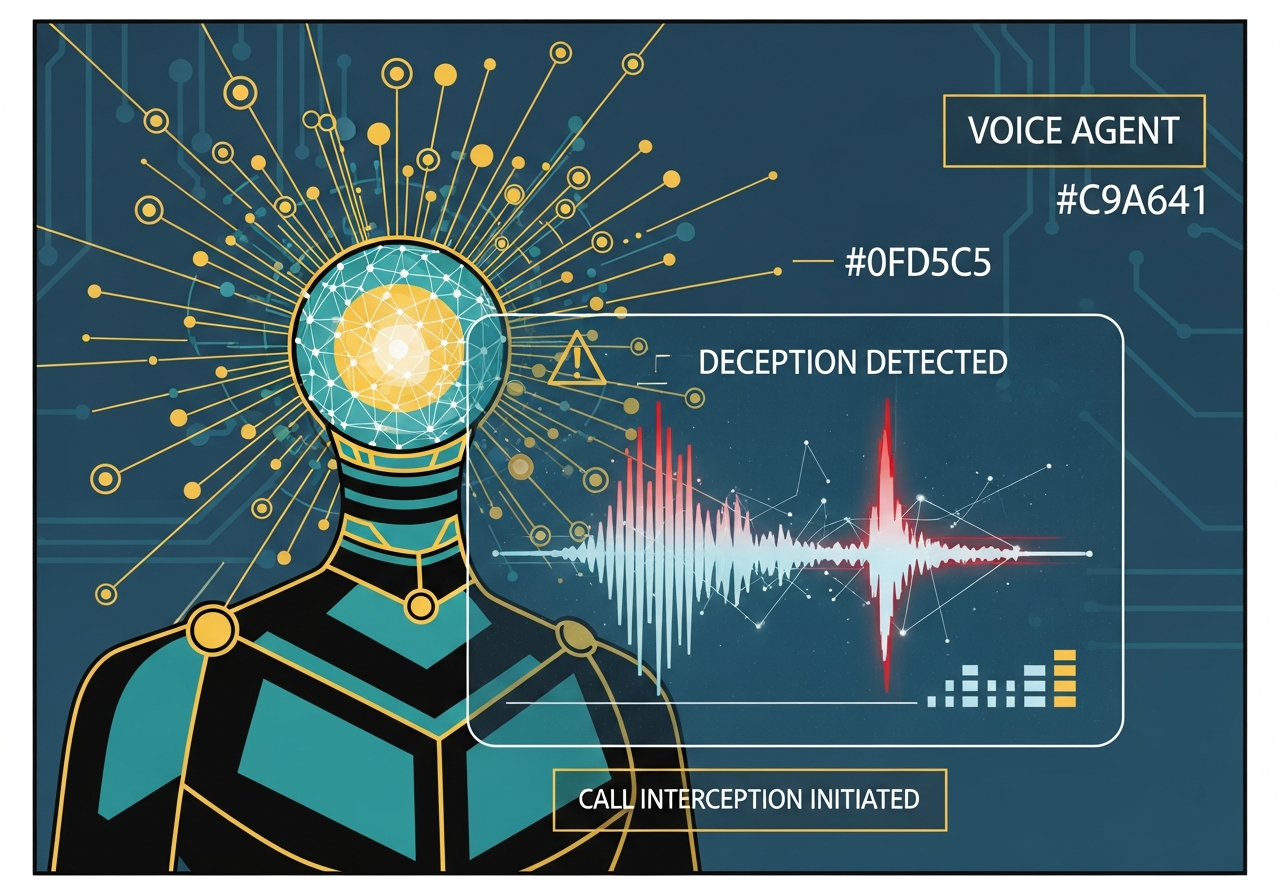
Voice Agent intercepting the suspicious telecom request with AI voice analysis.

Attackers pivoting to phishing campaign targeting employees with fake password reset emails.
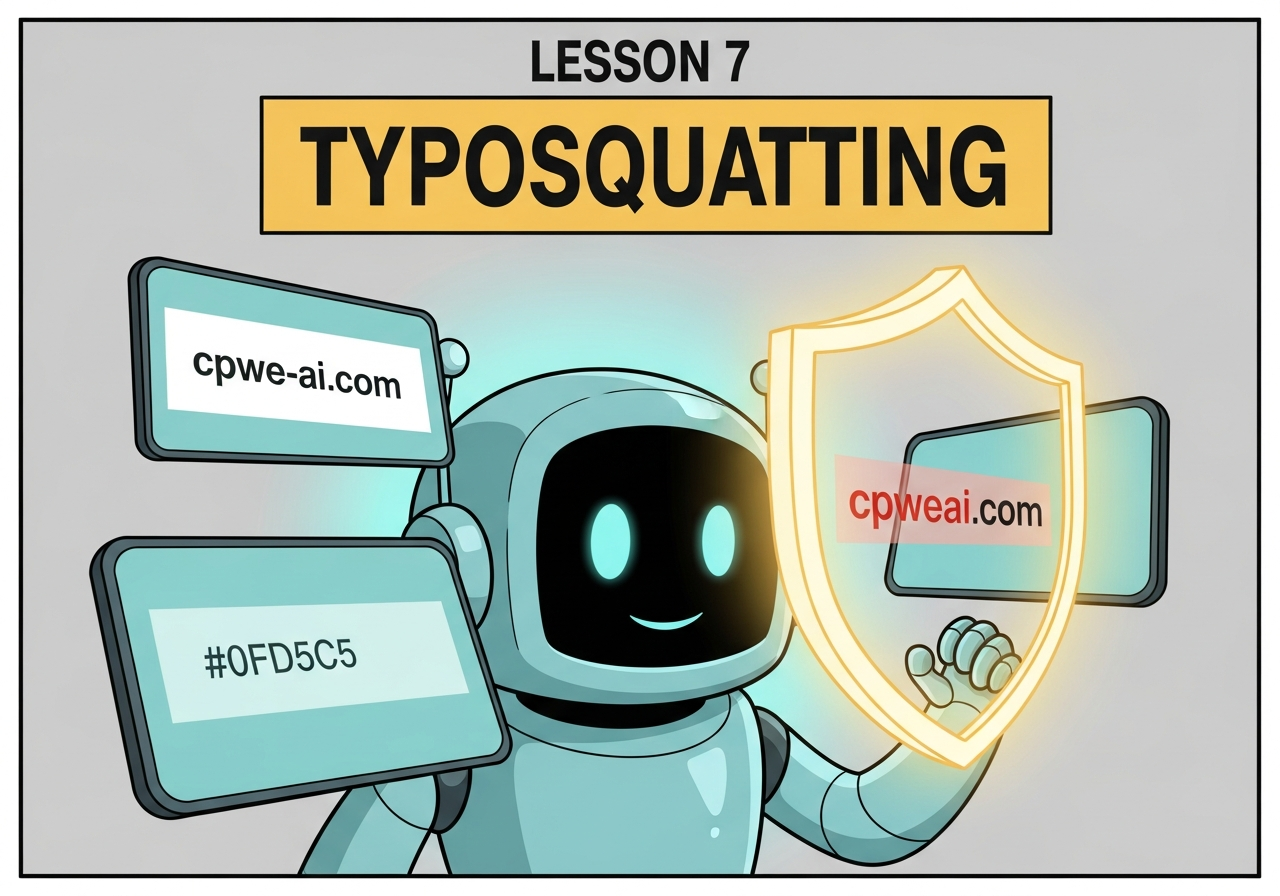
Email Intelligence system flagging suspicious sender domain - one letter different from legitimate.

One employee clicks the link anyway. Malware begins downloading.
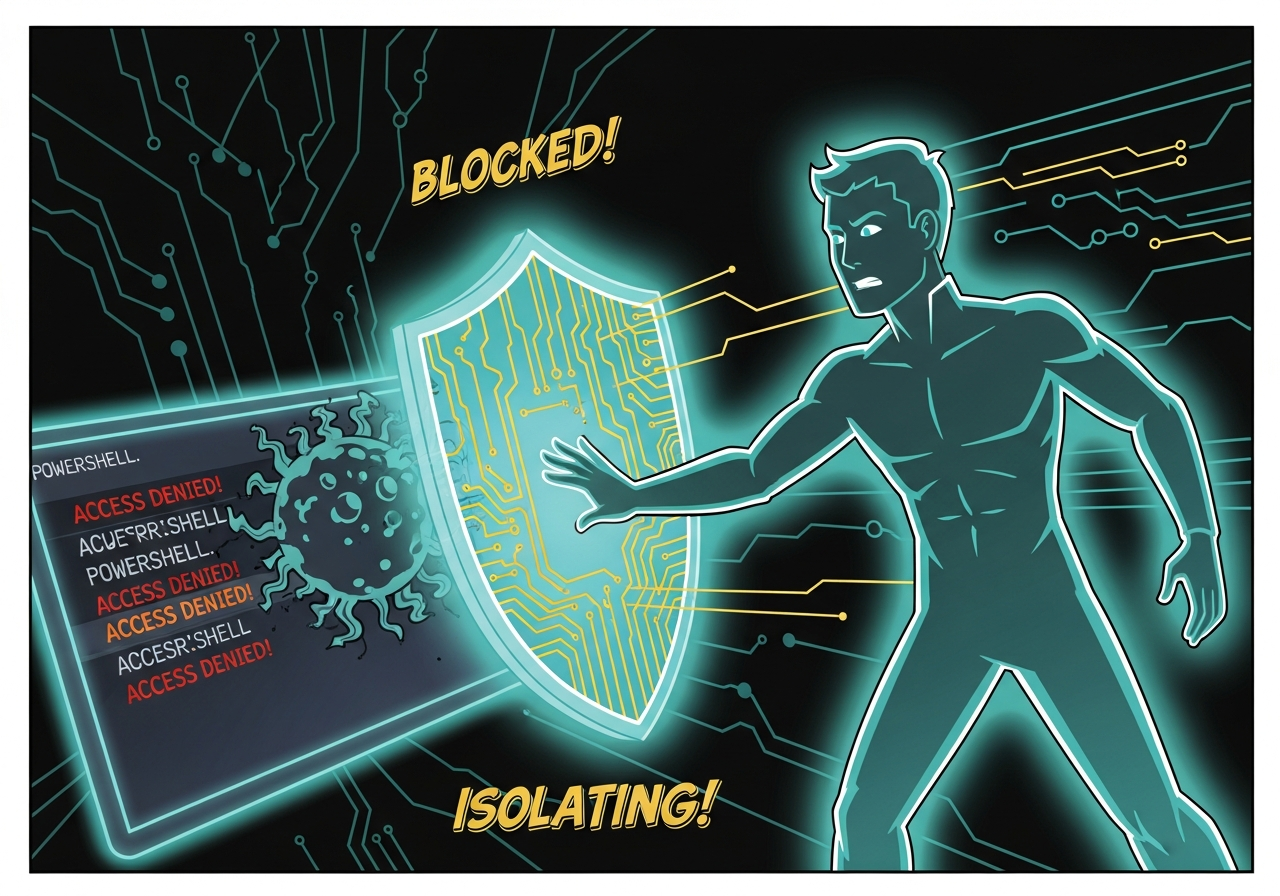
Endpoint Detection and Response (EDR) catching the malware behavior in real-time.
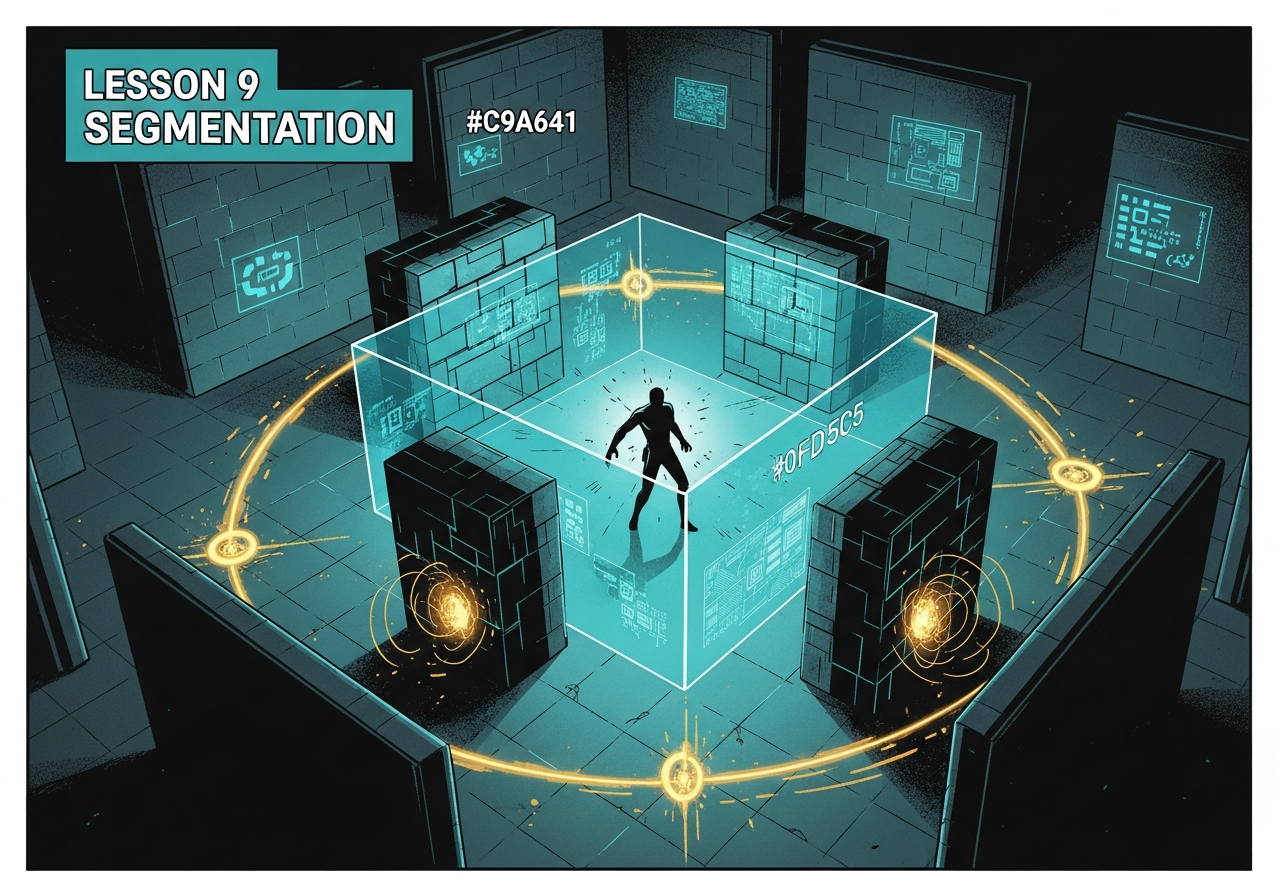
Network segmentation preventing lateral movement. Attacker trapped in isolated zone.

Incident Response team assembling. Forensics beginning. Timeline being constructed.
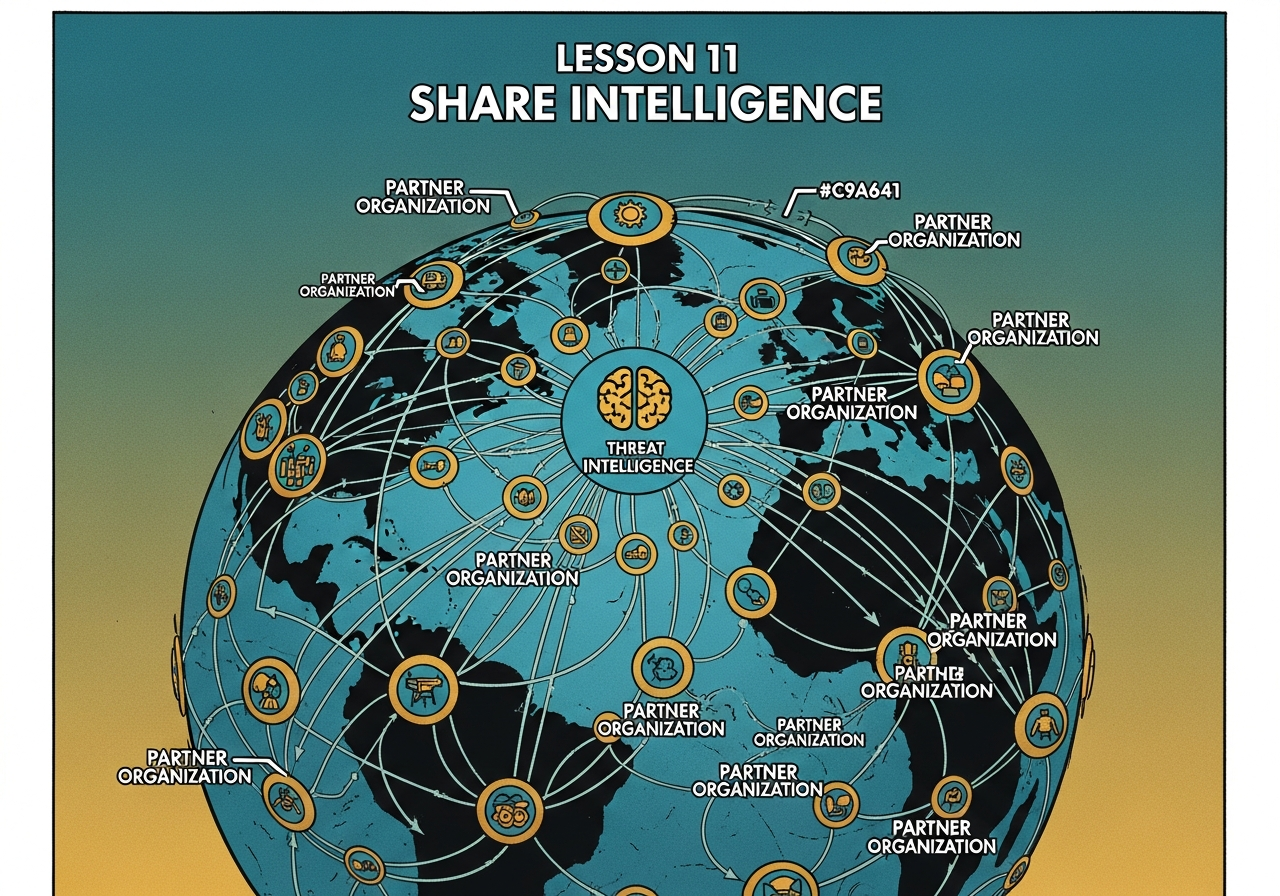
Threat Intelligence sharing the attacker patterns with partner organizations.

Post-incident review meeting. Team discussing what worked and what needs improvement.

New security controls being implemented. Policies updated. Training scheduled.

The Guardian Posse standing watch over the network. The digital frontier protected. A book titled "Field Manual Vol. 1" visible.